As generative AI technologies rapidly advance and become increasingly prevalent, the nature of the cyber war between attackers and defenders has evolved dramatically. Attackers are developing highly customized campaigns at machine speeds, rendering the time-tested and human-centric methodologies used by traditional defenses obsolete.
The central challenge facing today’s organization is no longer identifying vulnerabilities, but rather transforming security frameworks to utilize principles of Zero Trust architectures, cryptography, and empowering developers to implement these principles. Seven key paradigm shifts were identified through a synthesis of input from security architects, development leaders, and MLOps specialists. These shifts will enable organizations to develop resilience in this new era of cyber warfare.
Challenge #1: Transitioning the Role of Human Judgment to Cryptography in Defending Against Attacks
Generative AI is now capable of producing convincing phishing attacks and believable deepfakes, making traditional methods of educating end-users about recognizing suspicious communications ineffective. Machine-generated attacks are able to quickly evolve and outmaneuver human judgment and traditional training efforts.
Rather than relying on human judgment and education, organizations must implement defenses utilizing cryptographic verification and authentication techniques to verify identities within applications. Cryptographic verification provides a foundation upon which organizations can establish defenses against highly sophisticated and AI-generated social engineering tactics.
Floyd Clinton Te, Cyber Security Analyst at The Missing Link, who specializes in Security Operations Center (SOC) workflows, emphasizes that the priority isn’t just defense, it’s proactive adaptation through continuous, contextual training and utilizing Zero Trust architecture to contain the blast radius. He stresses that while AI detects patterns, human interpretation remains critical, demanding that analysts develop frontline skills like emotional intelligence and skepticism to spot subtle manipulation.
In addition to the human aspect, companies need to be able to switch their technical response to machine speed. Real-time threat intelligence should be integrated into current technology infrastructure within seconds -not hours or days- and this will enable companies to create a “cybersecurity immune system” using AI for defense, as well as how the use of quantum computing may impact future threats. (Thanasis Koufos, Cyber Security Enthusiast & External Partner at AspectSoft)
A layered technical response includes:
- Technical Verification (Cryptography): Implementing phishing-resistant elements (such as FIDO2 / PassKeys) for high-risk transactions.
- Behavioral Context Scoring: Translating focus from content-based filtering to combining AI-based email gateway products with session-based scoring of user sessions (device, location, typing cadence) to identify anomalies. (Yerbol Klimov, Founder/CEO of 360Solutions)
- Zero-Trust Communications Architecture: Developing communications architecture that analyzes signals beyond keyword-based searches to identify and flag anomalous behaviors. Furthermore, implementing out-of-band (OOB) verification requirements for requests involving credentials, money or sensitive data, which require approval via a separate, isolated system that cannot be circumvented by the compromised communication pathway. (Kumbhaj Shukla, Software Engineer at Paytm)
Challenge #2: Removing the Productivity Tax of Shift-Left Security
The shift-left initiative has historically failed due to the fact that it was implemented at developers, not for them, resulting in a “productivity tax” for developers to bear through the disruption of their “Flow State” caused by lengthy scans and excessive, low-priority alerts that result in fatigue.
Organizations must balance the need for security with the need to empower developers, creating a “paved road” where the path of least resistance is also the secure path. Establishing secure by design principles during early architectural planning is essential to preclude unnecessary rework and friction. (Kumbhaj Shukla, Software Engineer at Paytm; Thanasis Koufos, Cyber Security Enthusiast & External Partner at AspectSoft)
Specifically, Yerbol Klimov, recommends a successful model: “We use PR-level SAST /DAST in GitLab CI that auto-blocks only P1 / P2 findings; devs fix in less than 5 minutes via inline suggestions.”
Key strategies for creating invisible, platform-based guardrails, contextual, integrated development environment (IDE)-based tools, and invisible, platform-based guardrails include:
- Invisible, Platform-based Guardrails: Implementing non-negotiable security controls directly into platform components (i.e., Terraform templates that make it impossible to deploy an unauthenticated database).
- Contextual, IDE-integrated Tools: Providing real-time, actionable feedback to developers during the writing of code, similar to how code linting works. Specifically, this can include providing real-time suggestions of the most recent patch available for a vulnerable library.
- Defined Service-Level Agreements (SLAs): Establishing well-defined SLAs between engineering and security teams ensures tools provide actionable feedback and prevent security from becoming punitive, encouraging developer buy-in.
Challenge #3: Addressing the Privacy and Portability Challenges of Passwordless Identity
Passwordless technology presents a trade-off between the problems associated with managing passwords versus the “Walled Garden” and “Single Point of Failure” risks presented by using proprietary cloud sync services (i.e., Apple, Google, Microsoft) to store passkeys and authenticate users.
The major hurdle to addressing these issues is the risk of vendor lock-in in that it supports open standards as well as user-centered recovery procedures that are robust. Open standards and user-centered recovery procedures support a broad range of individuals with disabilities or temporary impairments that prevent them from using their devices; thus, there exists a need for technology/device-agnostic solutions to address the potential negative impacts of increased complexity of recovery from cyber attacks. (Thanasis Koufos, Cyber Security Enthusiast; Kumbhaj Shukla, Software Engineer at Paytm)
Strategies for mitigating the risk of vendor lock-in include:
- Exportable Credentials: Mandating the use of exportable WebAuthn credentials paired with recovery codes stored in an offline vault to ensure that privacy equals portability plus physical backup. (Yerbol Klimov, Founder/CEO of 360Solutions)
- Ecosystem-Agnostic Recovery: Building products that have recovery paths (e.g., “Social Recovery” or hardware-based recovery) that do not depend on a single vendor, thereby mitigating the catastrophic single-point-of-failure risks associated with vendor lock-in. (Kumbhaj Shukla, Software Engineer at Paytm)
- Transitional Bridges: Utilizing password managers as transitional bridges in mobile-first workflows, recognizing their continued role even in a passwordless environment.
- Explicit Migration: Building migration paths (i.e., “Passkey Migration” or “Export” flows) that are secure, easy to understand, and allow users to manage their digital identity as a first-class asset.
Challenge #4: Retaining Human Judgment in Automated API Security
While automated tools excel at detecting technical anomalies (i.e., SQL injection), they are very poor at detecting business logic anomalies since they are context-less. For example, this may result in a coupon enumeration attack being missed by a “black box” tool.
The essential human component of API security is centered on performing business logic testing and threat modeling. Since automated tools cannot evaluate business logic authorization flaws (BFLA), where a user although authenticated is violating the application’s internal policies, organizations should automate the execution of testing and not judgment. (Kumbhaj Shukla, Software Engineer at Paytm)
According to Dimitrios S. Sfyris, Founder/Lead Developer at AspectSoft, expert in API architecture, API tools should include interpretability and transparency, and organizations should proactively tag APIs according to risk and sensitivity.
Key strategies for developing a human-in-the-loop feedback loop:
- API Threat Modeling in SDLC: Integrate API threat modeling and security activities across all phases of the Software Development Life Cycle (SDLC).
| SDLC Phase | Security Activities Example |
| Requirements | Defining security requirements (i.e. compliance, data protection) |
| Design | Threat modeling, designing a secure architecture |
| Implementation | Static code analysis, utilizing secure coding libraries |
| Testing | Vulnerability scanning, penetration testing, fuzz testing |
| Deployment | Hardening configurations, secrets management, controlling the CI/CD pipeline |
| Maintenance | Patching, monitoring, incident response |
- Explainable AI (XAI): Transforming the “Anomaly Blocked” message into detailed, explainable rules logs (i.e., “Rate Limit Triggered: 400 RPM from IP X”), detailing the deviations from the user behavioral baseline. (Yerbol Klimov, Founder/CEO of 360Solutions; Kumbhaj Shukla, Software Engineer at Paytm)
- Human-AI Partnership: The human subject reviews the explainable data to determine whether to train the AI (in the event of a false positive) or escalate to a full incident (in the event of a true positive). This partnership enables the automation of noise while preserving the intellect of humans to address contextual threats.
Challenge #5: Identifying Areas Where Zero-Trust Fails in Real World Environments
Zero Trust (ZT) is commonly misinterpreted as simply replacing the perimeter VPN. However, the greatest strategic failures occur in the Developer Experience (DX) layer and the application/authorization layer itself. The “Clunky VPN” problem” — where developers are granted “all-or-nothing” access to systems — directly contradicts the core principle of ZT — least privilege. (Kumbhaj Shukla, Software Engineer at Paytm)
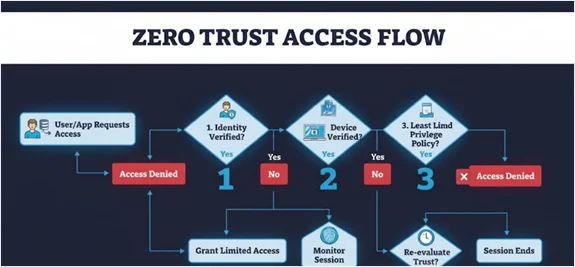
To overcome these strategic failures, organizations must address specific, practical implementation errors. Dimitrios S. Sfyris, Founder/Lead Developer at AspectSoft, and Thanasis Koufos, Cyber Security Enthusiast & External Partner at AspectSoft, assert: “Common implementation errors include overly permissive service accounts, flat network architectures, and token sprawl in cloud-native environments. To achieve true Zero Trust, organizations must apply the same rigor to developer access and toolchains as they do to production code pipelines.”
To move beyond these errors, the following Just-in-Time (JIT) implementation controls are recommended:
- Short-Term, Access-Scope Based Credentials: Generating dynamic, short-term (i.e., 15 minute) credentials with access scopes to only allow access to the minimum required resources (i.e., READ access to a specific database table). This removes static passwords or API Keys from production environments. (Kumbhaj Shukla, Software Engineer at Paytm)
- Ephemeral Tokens and OIDC: Requiring ephemeral JWTs tied to modern identity protocols (i.e., GitHub Actions OIDC). (Yerbol Klimov, Founder/CEO of 360Solutions)
- Service-to-Service mTLS: Utilizing a service mesh (i.e., Istio or Linkerd) to enforce Mutual TLS, where each service must provide proof of identity to prevent lateral movement after a compromise.
- Code Signing and Endpoint Telemetry: Implementing code signing and artifact integrity checking and utilizing endpoint telemetry (runtime behavior monitoring) for developer laptops.
The strategic takeaway is that least privilege must be applied on a per-build and per-session basis, and validated dynamically.
Challenge #6: Protecting the Probabilistic AI Supply Chain
Due to the probabilistic and opaque nature of models, the AI supply chain is far more fragile than the code supply chain. The two most significant risks facing organizations are targeted data poisoning (i.e., subtly corrupting training data to elicit malicious behavior, e.g., deceiving a self-driving vehicle) and non-malicious model drift (i.e., the world changing and the model’s predictions deviating from reality).
Protecting the AI pipeline requires a focus on both data provenance tracking and continuous inference monitoring. Defense-in-depth approaches (i.e. isolate environments and least privilege access to training data) are equally critical to securing the AI pipeline. Experts agree that securing the AI supply chain requires treating AI assets as rigorously as code: “Treat Prompts Like Code — Sign, Version, Audit.” (Yerbol Klimov, Founder/CEO of 360Solutions; Thanasis Koufos, Cyber Security Enthusiast & External Partner at AspectSoft; Kumbhaj Shukla, Software Engineer at Paytm; Dimitrios S. Sfyris, Founder/Lead Developer at AspectSoft)
Key MLOps security controls include:
- Data Provenance & Lineage: Utilizing tools (i.e., DVC) to create a complete, auditable record of data origin, labeling and versioning. This is the primary method to defend against data poisoning.
- Validation Gates for Data: Implement validation gates to filter and sanitize training and fine-tune data before it is fed to the model.
- Adversarial Validation (Staging): Performing red teaming on the model in a safe environment and feeding the model known poisoned or junk data to test the model’s resiliency prior to deploying.
- Continuous Production Drift Monitoring: Ongoing monitoring of the statistical characteristics of the model’s inputs and outputs. When the model’s confidence levels drop or the distribution of predictions shift, the model has drifted and an alert will be generated to trigger either a retrain or investigation.
- Automated Rollback: Reliance on canary inputs that generate alerts when the model drifts by more than 3%, and utilizing automated rollback procedures to revert back to the most recently trusted version of the model. (Yerbol Klimov, Founder/CEO of 360Solutions)
Challenge #7: Measuring Security Culture over Compliance
Compliance represents a “floor”, whereas the “ceiling” is a function of security culture. Therefore, “check-box security” produces a false sense of security, as organizations can be completely compliant while practicing brittle security.
To measure a genuine cultural transformation, security leaders must emphasize leading metrics that represent ownership and velocity driven by engineers. The behavioral aspect is critical: “It’s not just ‘Did we follow the process?’, but ‘Were we concerned enough to improve it?'” (Floyd Clinton Te, Cyber Security Analyst at The Missing Link; Kumbhaj Shukla, Software Engineer at Paytm)
Metrics representing genuine cultural transformation include:
- Mean Time to Remediate (MTTR): The single most important metric representing a cultural transformation. Low MTTR indicates that developers view security fixes as high priority “production-down” bugs, demonstrating ownership and high velocity. (Kumbhaj Shukla, Software Engineer at Paytm; Yerbol Klimov, Founder/CEO of 360Solutions, measures MTTR for self-reported issues to < 48 hours)
- Security Engagement & Champions: Moving past “training completed” to quantify the degree of positive engagement, such as the number of high-quality internal security reports submitted by employees outside of the security team, or the existence of “Security Champions” who are willing to promote best practices from within the product teams.
- Voluntary Contributions to Security: The ultimate level of maturity is when an engineer, without prompting, places work on their own roadmap to remediate security debt. This can be measured by tracking the percentage of engineers who submit voluntary security PRs (360Solutions achieved 42% visibility). (Kumbhaj Shukla, Software Engineer at Paytm; Yerbol Klimov, Founder/CEO of 360Solutions)
Conclusion: The Architectural Imperative
The realities of cybersecurity today are clear: the perimeter is dead; the human is the new vulnerability; and AI is both the greatest threat and the greatest tool. Organizations that will succeed will be those deliberately and architecturally shifting their approach — moving from trust-based access to Zero Trust authorization, from human-based detection to cryptographic-based verification, and from compliance as a check list to security as an engineering discipline. The future of resilience will exist in embedding security as part of the core engineering culture and as part of the application itself.
Acknowledgements and Contributor List
This comprehensive analysis was made possible through the collaboration and expert insights of leading practitioners from across the industry:
- Floyd Clinton Te: Cyber Security Analyst, The Missing Link
- Kumbhaj Shukla: Software Engineer, Paytm
- Thanasis Koufos: Cyber Security Analyst & External Partner, AspectSoft
- Yerbol Klimov: Founder & CEO, 360Solutions
- Dimitrios S. Sfyris: Founder & Lead Developer, AspectSoft
Subscribe to our newsletter!








+ There are no comments
Add yours